Network Notepad Professional Cracked
New Pages
- Diamondback Mountain Bike Serial Numbers
- Download Labview Software Free
- Metal Slug 3 Emulator
- Asus Data Security Manager Tray
- Sony Vegas Pro 11 Transitions
- I Am Alive Reloaded Crack Fix
- Very Best Of Dusty Springfield Pdf
- Avg Pc Tuneup License Code Crack Serial Keygen
- Hp Compaq Dx2000 Mt Drivers Windows Xp
- Calculus Made Easy Crack Key Generator
- Install Linux On Usb Drive
- Hog Ultimate Collection
- Itchy Fungus Between Fingers
- Best English Grammar Book In Hindi Pdf Free Download
- Download Sql Server 2000 Personal Edition 64 Bit
- Download Pearl From The Landlord
Network Notepad Professional Cracked
The Locky Ransomware Encrypts Local Files and Unmapped Network Shares. A new ransomware has been discovered called Locky that encrypts your data using AES encryption and then demands. Though the ransomware sounds like one named by my kids, there is nothing childish about it. It targets a large amount of file extensions and even more importantly, encrypts data on unmapped network shares. Encrypting data on unmapped network shares is trivial to code and the fact that we saw the recent DMA Locker with this feature and now in Locky, it is safe to say that it is going to become the norm. Like Crypto. Wall, Locky also completely changes the filenames for encrypted files to make it more difficult to restore the right data. At this time, there is no known way to decrypt files encrypted by Locky. For those who wish to discuss this ransomware or have questions, please feel free to post in our Locky Ransomware Support and Help Topic. Locky installed via fake invoices. Locky is currently being distributed via email that contains Word document attachments with malicious macros. The email message will contain a subject similar to ATTN Invoice J 9. Please see the attached invoice Microsoft Word Document and remit payment according to the terms listed at the bottom of the invoice. We dont know much about computer hacking here at Cracked, because that stuff involves numbers, but weve come across a whole bunch of different crazy brain and body. File For Pa Partial Unemployment. Network Notepad Professional Cracked Windshield' title='Network Notepad Professional Cracked Windshield' />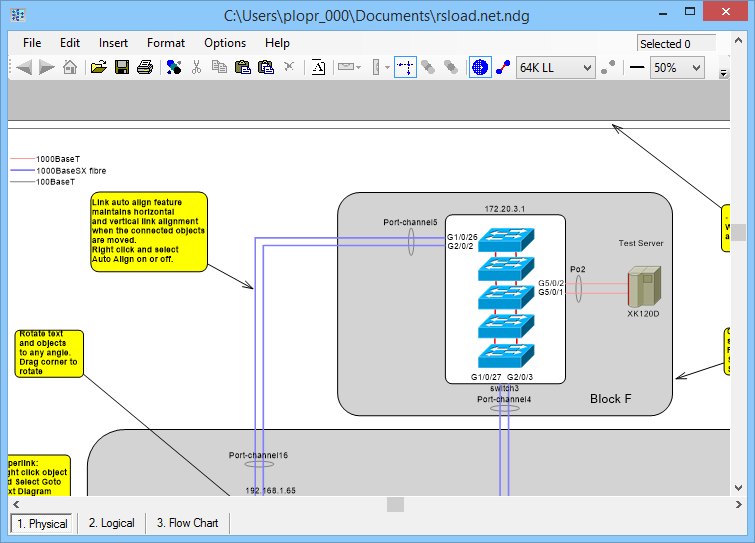 Network Notepad Professional Cracked RibsNetwork Notepad Professional Cracked ScreenAll that strange computer jargon turned into plain English. Questions and Answers from the Community. Maybe the size of mouse you are giving him is too big. Make sure the mouse is hot enough. Harden Windows 10 A Security Guide gives detailed instructions on how to secure Windows 10 machines and prevent it from being compromised. We will harden the system. In case you havent noticed, we here at Lifehacker have spent the day gleefully reveling in fullblown Eclipse Madness. But now that the blessed event is behind us. A new ransomware has been discovered called Locky that encrypts your data using AES encryption and then demands. Though the. The solar eclipse is rapidly approaching and, for the towns that happen to be in the narrow 70mile band of best observation, this means gearing up for quite the. An example of one of these emails can be seen below. Attached to these email messages will be a malicious Word document that contains a name similar to invoiceJ 1. When the document is opened, the text will be scrambled and the document will display a message stating that you should enable the macros if the text is unreadable. Once a victim enables the macros, the macros will download an executable from a remote server and execute it. The file that is downloaded by the macro will be stored in the Temp folder and executed. This executable is the Locky ransomware that when started will begin to encrypt the files on your computer. Locky encrypts your data and completely changes the filenames. When Locky is started it will create and assign a unique 1. F6. 70. 91. F1. D2. A9. 22. B. Locky will then scan all local drives and unmapped network shares for data files to encrypt. When encrypting files it will use the AES encryption algorithm and only encrypt those files that match the following extensions. ARC,. PAQ,. tar. NEF,. MYI,. MYD,. frm,. SQLITEDB,. SQLITE3,. Security copy,. DOT,. CSV,. uot,. RTF,. XLS,. PPT,. stw,. DOC,. pem,. csr,. Furthermore, Locky will skip any files where the full pathname and filename contain one of the following strings tmp, winnt, Application Data, App. Data, Program Files x. Program Files, temp, thumbs. Recycle. Bin, System Volume Information, Boot, Windows. When Locky encrypts a file it will rename the file to the format uniqueididentifier. So when test. jpg is encrypted it would be renamed to something like F6. F1. D2. 4A9. 22. B1. Bambi Felix Salten First Edition here. A7. FC2. 7E1. 9A9. D9. BC. locky. The unique ID and other information will also be embedded into the end of the encrypted file. It is important to stress that Locky will encrypt files on network shares even when they are not mapped to a local drive. As predicted, this is becoming more and more common and all system administrators should lock down all open network shared to the lowest permissions possible. As part of the encryption process, Locky will also delete all of the Shadow Volume Copies on the machine so that they cannot be used to restore the victims files. Komik Manga Serial Cantik more. Locky does this by executing the following command vssadmin. Delete Shadows All Quiet. In the Windows desktop and in each folder where a file was encrypted, Locky will create ransom notes called Lockyrecoverinstructions. This ransom note contains information about what happened to the victims files and links to the decrypter page. Locky will change the Windows wallpaper to Userp. ProfileDesktopLockyrecoverinstructions. Last, but not least, Locky will store various information in the registry under the following keys HKCUSoftwareLockyid The unique ID assigned to the victim. HKCUSoftwareLockypubkey The RSA public key. HKCUSoftwareLockypaytext The text that is stored in the ransom notes. HKCUSoftwareLockycompleted Whether the ransomware finished encrypting the compute. The Locky Decrypter Page. Inside the Locky ransom notes are links to a Tor site called the Locky Decrypter Page. This page is located at 6dtxgqam. Once a victim sends payment to the assigned bitcoin address, this page will provide a decrypter that can be used to decrypt their files. Locky related FilesUserp. ProfileDesktopLockyrecoverinstructions. Userp. ProfileDesktopLockyrecoverinstructions. Temprandom. exe. Locky related Registry entries. HKCUSoftwareLocky. HKCUSoftwareLockyid. HKCUSoftwareLockypubkey. HKCUSoftwareLockypaytext. HKCUSoftwareLockycompleted1. HKCUControl PanelDesktopWallpaperUser. ProfileDesktopLockyrecoverinstructions.
Network Notepad Professional Cracked RibsNetwork Notepad Professional Cracked ScreenAll that strange computer jargon turned into plain English. Questions and Answers from the Community. Maybe the size of mouse you are giving him is too big. Make sure the mouse is hot enough. Harden Windows 10 A Security Guide gives detailed instructions on how to secure Windows 10 machines and prevent it from being compromised. We will harden the system. In case you havent noticed, we here at Lifehacker have spent the day gleefully reveling in fullblown Eclipse Madness. But now that the blessed event is behind us. A new ransomware has been discovered called Locky that encrypts your data using AES encryption and then demands. Though the. The solar eclipse is rapidly approaching and, for the towns that happen to be in the narrow 70mile band of best observation, this means gearing up for quite the. An example of one of these emails can be seen below. Attached to these email messages will be a malicious Word document that contains a name similar to invoiceJ 1. When the document is opened, the text will be scrambled and the document will display a message stating that you should enable the macros if the text is unreadable. Once a victim enables the macros, the macros will download an executable from a remote server and execute it. The file that is downloaded by the macro will be stored in the Temp folder and executed. This executable is the Locky ransomware that when started will begin to encrypt the files on your computer. Locky encrypts your data and completely changes the filenames. When Locky is started it will create and assign a unique 1. F6. 70. 91. F1. D2. A9. 22. B. Locky will then scan all local drives and unmapped network shares for data files to encrypt. When encrypting files it will use the AES encryption algorithm and only encrypt those files that match the following extensions. ARC,. PAQ,. tar. NEF,. MYI,. MYD,. frm,. SQLITEDB,. SQLITE3,. Security copy,. DOT,. CSV,. uot,. RTF,. XLS,. PPT,. stw,. DOC,. pem,. csr,. Furthermore, Locky will skip any files where the full pathname and filename contain one of the following strings tmp, winnt, Application Data, App. Data, Program Files x. Program Files, temp, thumbs. Recycle. Bin, System Volume Information, Boot, Windows. When Locky encrypts a file it will rename the file to the format uniqueididentifier. So when test. jpg is encrypted it would be renamed to something like F6. F1. D2. 4A9. 22. B1. Bambi Felix Salten First Edition here. A7. FC2. 7E1. 9A9. D9. BC. locky. The unique ID and other information will also be embedded into the end of the encrypted file. It is important to stress that Locky will encrypt files on network shares even when they are not mapped to a local drive. As predicted, this is becoming more and more common and all system administrators should lock down all open network shared to the lowest permissions possible. As part of the encryption process, Locky will also delete all of the Shadow Volume Copies on the machine so that they cannot be used to restore the victims files. Komik Manga Serial Cantik more. Locky does this by executing the following command vssadmin. Delete Shadows All Quiet. In the Windows desktop and in each folder where a file was encrypted, Locky will create ransom notes called Lockyrecoverinstructions. This ransom note contains information about what happened to the victims files and links to the decrypter page. Locky will change the Windows wallpaper to Userp. ProfileDesktopLockyrecoverinstructions. Last, but not least, Locky will store various information in the registry under the following keys HKCUSoftwareLockyid The unique ID assigned to the victim. HKCUSoftwareLockypubkey The RSA public key. HKCUSoftwareLockypaytext The text that is stored in the ransom notes. HKCUSoftwareLockycompleted Whether the ransomware finished encrypting the compute. The Locky Decrypter Page. Inside the Locky ransom notes are links to a Tor site called the Locky Decrypter Page. This page is located at 6dtxgqam. Once a victim sends payment to the assigned bitcoin address, this page will provide a decrypter that can be used to decrypt their files. Locky related FilesUserp. ProfileDesktopLockyrecoverinstructions. Userp. ProfileDesktopLockyrecoverinstructions. Temprandom. exe. Locky related Registry entries. HKCUSoftwareLocky. HKCUSoftwareLockyid. HKCUSoftwareLockypubkey. HKCUSoftwareLockypaytext. HKCUSoftwareLockycompleted1. HKCUControl PanelDesktopWallpaperUser. ProfileDesktopLockyrecoverinstructions.